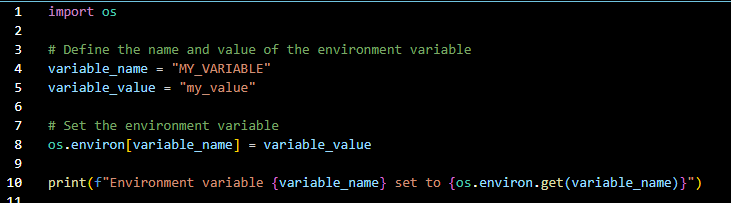
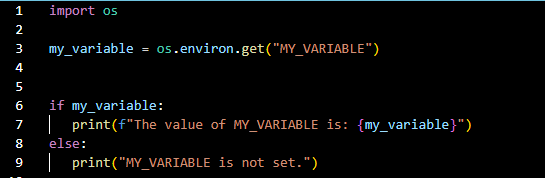
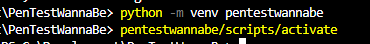
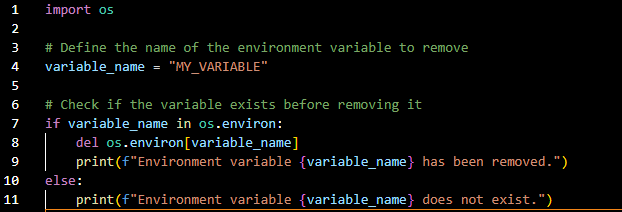
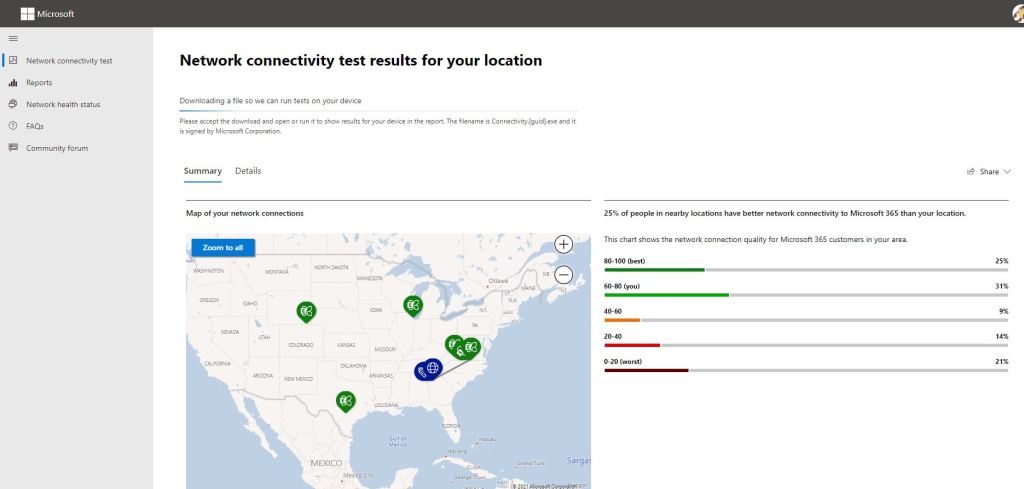
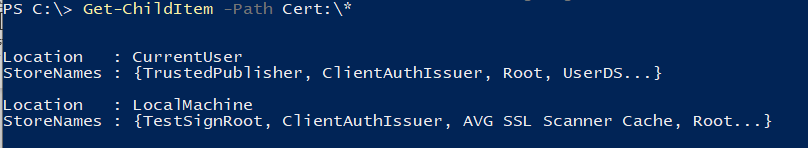
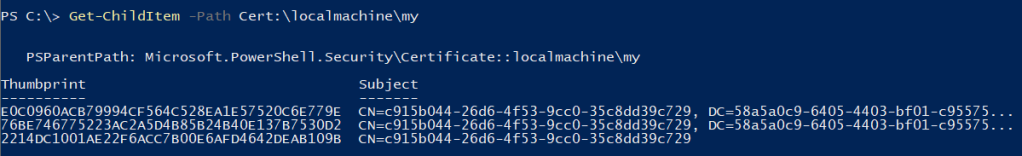
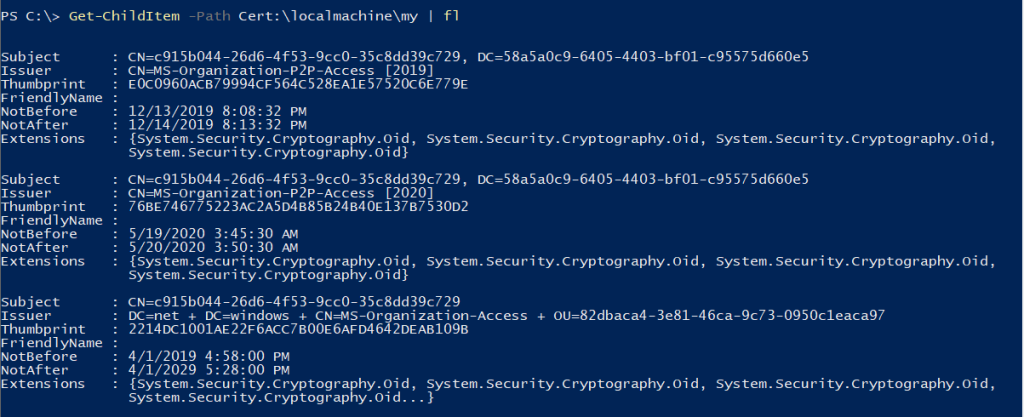
Cross-Site Request Forgery (CSRF) is a security vulnerability that poses a significant threat to web applications. CSRF attacks occur when an attacker tricks a user’s browser into making an unintentional and unauthorized request on behalf of the user.
To mitigate this risk, web developers often employ CSRF tokens as a fundamental security measure. In this article, we will delve into the benefits of CSRF tokens and how they contribute to enhancing web application security.
- Preventing Unauthorized Requests: CSRF tokens serve as a protective barrier against unauthorized requests. By embedding a unique token in each form or request, web applications can verify the legitimacy of the incoming requests. This ensures that only requests originating from the same site and user are processed, preventing attackers from forging requests on behalf of users.
- Enhancing User Authentication: CSRF tokens complement user authentication mechanisms. Even if a user is authenticated, an attacker cannot exploit their active session to perform malicious actions without the corresponding CSRF token. This dual-layered security approach fortifies the overall protection of user accounts.
- Securing Sensitive Actions: CSRF tokens are particularly crucial when users perform sensitive actions, such as changing passwords, making financial transactions, or modifying account settings. Incorporating CSRF tokens into these processes adds an extra layer of security, ensuring that only intentional and authorized actions are carried out.
- Cross-Origin Protection: One of the primary benefits of CSRF tokens is their ability to safeguard against cross-origin attacks. By tying the token to the specific origin of the web application, attackers attempting to forge requests from a different domain are thwarted. This helps maintain the integrity of the web application and prevents unauthorized cross-origin requests.
- Preventing Session Hijacking: CSRF tokens play a role in preventing session hijacking attempts. Since these tokens are typically bound to a user’s session, even if an attacker manages to obtain a user’s session identifier, they would still need the corresponding CSRF token to execute malicious actions. This adds an additional layer of complexity for attackers attempting to compromise user sessions.
- Compliance with Security Best Practices: CSRF token usage aligns with established security best practices. Many security standards and frameworks, such as OWASP (Open Web Application Security Project), recommend the implementation of CSRF protection mechanisms. Adhering to these guidelines not only helps protect users but also demonstrates a commitment to security excellence.
Conclusion:
In the ever-evolving landscape of web security, CSRF tokens stand out as a robust defense mechanism against unauthorized and malicious activities. By implementing CSRF tokens, web developers can fortify their applications, safeguard user data, and provide a secure online experience. As cyber threats continue to evolve, the proactive integration of CSRF tokens remains a crucial element in the ongoing effort to enhance web application security.